The Virtual Virus: Cybersecurity Threats
June 26, 2020 by Clara Kobashigawa

As we fight viruses in the physical and digital world, knowledge of these key concepts and tricks is crucial to protect yourself from a cyberattack. Phishing, defined as sending emails from accounts mimicking a reputable email to scam individuals, is incredibly common. Ransomware attacks, malicious software that blocks access to data until you pay, are also spreading throughout the virtual world. By equipping yourself and your community with these tips, you can best prepare for and detect an attack.
We compiled tips and tricks from Tyler’s Director of Tyler Detect Ron Bernier, on how to “hack hackers” from his recent webinar with National Association of Counties Tech Xchange titled, "Tips to Defend your Network Against Cyber Attacks (With Tyler Technologies)."
Passwords:
While you may roll your eyes at the idea of passwords, they play a crucial role in protecting your accounts.
- Roughly 1% of users have a password modeled after a patter like this: current season, year, capital letter -- Summer 2020. Don’t be that 1%.
- Do not reuse passwords. While this is difficult, use a password saver to make this precaution easier.
- Do not use a company email or account password for your personal devices and avoid using the same username for different logins as well.
Phishing:
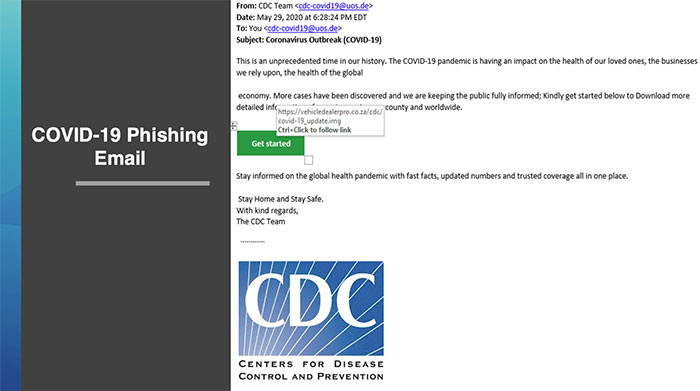
It is important to possess the skill of differentiating a phishing email vs a regular email.
- Hover mouse over the action block for hyperlink WITHOUT clicking the link. Therefore, you can see where the email is taking you and if the website looks reliable.
- Look at the entire email address, not just the contact name.
- Ask yourself, what are they trying to do? Exhort valuable information such as an SNN? Make you download something malicious, like a virus?
Multi-Factor Authentication:
While some argue that installing multi-factor authentication slows down productivity, the safety precautions outweigh the few extra minutes.
- It is relatively cheap and simple to implement, so there is no excuse not to have this.
- Installing the process can prevent against attacks and make it more challenging for hackers to infiltrate your systems.
- It adds an extra layer of protection and prevention against data breaches.
With threats frequently populating the internet, it is challenging to be aware about everything that is going on. Subscribe to Tyler’s Daily Threat Intelligence Briefing to stay informed. Email DailyThreatBrief@tylertech.com and request to be added to the distribution list and receive in your inbox every business day!