Use a Risk-Based Cybersecurity Approach
June 14, 2021 by Meredith Trimble

Building cybersecurity resilience in public agencies and schools has never been more important. Government-focused ransomware attacks were rampant in 2020, and there is no way to predict what new threats governments will face even in the months to come. Because the risk environment is always evolving, agencies must be able to prepare for and adapt to changing conditions in order to detect threats and recover rapidly from disruptions.
The recent webinar, “Achieving Cybersecurity Resilience Using a Risk-Based Approach,” outlined the elements of a holistic cybersecurity strategy and paid special attention to the benefits of a risk-based approach for the best ROI.
Following are some key takeaways from the session:
- A Repeatable, Sustainable Approach
Cybersecurity is a cross-functional responsibility starting at the top with executive leadership and includes all disciplines. Cybersecurity maturity models follow a scale of three functional elements — people, process, and technology — through objectives from foundational steps to repeatable, sustainable processes. It’s really an ongoing lifecycle approach in which organizations are constantly assessing and adjusting to an evolving context.
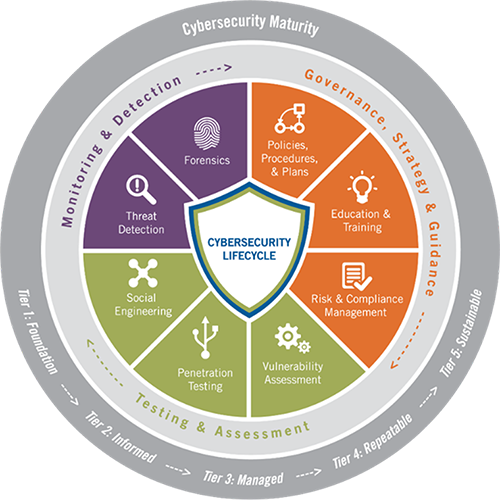
Tyler Cybersecurity Lifecycle
- Elements of a Holistic Strategy
Cybersecurity is not just an IT issue. Rather, cybersecurity should be an institutionalized part of the entire organization. In the case of mitigating risk, the whole is greater than the parts; they all build from and reinforce each other. The critical parts include:
- People culture. Leadership sets the tone and leads by example. Hiring includes cybersecurity in job descriptions and there is training for everyone with performance tied to compensation.
- Process culture. “Every process should include learning and improvement,” noted webinar presenter, Brendan D. Travis, director of business development, Tyler Cybersecurity. “Every process should be comprised of accountability touch-points and provide end-to-end corroboration of the function it represents.” This includes user and equipment provisioning, change management, and comprehensive cyber risk management processes including account and activity review.
- Technology culture. Avoid a false sense of security by layering shiny new technology over an inefficient operation. Technology culture with a layered approach to cybersecurity includes perimeter preventative controls, zero-day protection, and multi-factor authentication, among other controls.
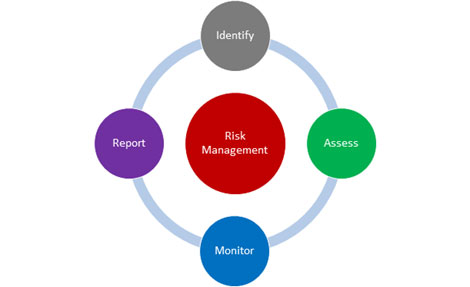
- Risk Management
Organizations need a mechanism for calculating and quantifying where risk lies. Identifying risks up front, having a process for assessing the likelihood those events will come to fruition, monitoring the effectiveness of controls in place that mitigate risks, and reporting out on those controls are key components to continuous risk management.
- Context in Remediation
Keep in mind context matters. When an organization identifies a risk, a recommendation on how to remediate that naturally follows. There are considerations, however, in determining how to remediate or mitigate risk. Those include the amount of time, money, and available skill set involved. A cost-benefit analysis may be appropriate for calculating risk and associated resource requirement.
Striving to mitigate risk is a moving target and unique to every organization. The overarching goal is to reduce the likelihood your agency will be negatively impacted by a cybersecurity event. A risk-based approach can help solidify a successful cybersecurity strategy particularly in the heightened and evolving threat environment.